Comprehensive Security Operations Center (SOC) Training and Certification in Minnesota
Unlock your career potential with CareerMaker Solutions’ comprehensive SOC Training Programs in Minnesota. Our SOC Analyst Training in Minnesota offers practical knowledge and hands-on experience in threat detection, incident response, and cybersecurity management. Tailored for both beginners and experienced professionals, our SOC certification Minnesota program equips you with the essential skills needed to excel in today’s rapidly evolving security landscape. With expert-led courses and real-world scenarios, you’ll gain the expertise necessary to safeguard critical digital assets. Enroll today and take the next step in advancing your cybersecurity career!
Years in IT training industry
IT professional Trained
Countries
Bootcamps
- TRUSTED BY -










- SOC COURSE HIGHLIGHTS -

SOC Certification Training Highlights with CareerMaker:
Comprehensive Curriculum: Our SOC (Security Operations Center) certification training offers a thorough, up-to-date curriculum covering essential areas such as threat detection, incident response, security monitoring, and more. This ensures you’re well-prepared to tackle real-world challenges in cybersecurity.
Hands-on Experience: Gain practical skills through real-world simulations and hands-on labs, equipping you to effectively manage and mitigate security threats across diverse environments.
Expert Instructors: Learn from seasoned cybersecurity professionals with extensive experience in SOC operations. Their valuable insights and practical guidance will equip you with the tools for success in your career.
Flexible Learning Options: Choose from online, in-person, and hybrid learning formats, allowing you to customize your learning experience to fit your schedule and personal learning style, making it easier to balance training with your lifestyle.
Career Support: Access career guidance, resume-building workshops, and job placement assistance to fast-track your path toward a successful career in cybersecurity.
Industry-Recognized Certification: Earn a SOC certification recognized by top organizations in the cybersecurity field, enhancing your professional credibility and unlocking more job opportunities.
Networking Opportunities: Connect with peers, mentors, and industry experts through our platform, expanding your professional network and building valuable relationships within the cybersecurity community.
- Upcoming Live BOOTCAMP CALENDAR -
Class Schedule
| 08:00 AM-10:00 AM(EST) | Weekend Evening | October 26 2024 - November 24 2024 | Live Online | $1200 STUDY NOW PAY LATER | INQUIRY NOW |
| 05:00 PM-08:00 PM(CST) | Weekend Evening | October 26 2024 - November 24 2024 | Live Online | $1200 STUDY NOW PAY LATER | INQUIRY NOW |
| 10:00 AM to 06:00PM(CST) | Weekdays | October 07 2024- November 02 2024 | Live Online | $1200 STUDY NOW PAY LATER | INQUIRY NOW |
October 26 2024 To November 24 2024
October 26 2024 To November 24 2024
October 07 2024 To November 02 2024
-Security Operation Center Training Program -
A Security Operations Center (SOC) is a specialized team responsible for overseeing and managing an organization's security operations, addressing both technical and operational concerns. The SOC works around the clock to monitor systems, detect potential threats, and respond to security incidents in real-time. Its core mission is to protect the organization's digital assets by proactively defending against cyberattacks, ensuring the safety and integrity of critical information and infrastructure.
Continuous Monitoring: The SOC team consistently monitors the organization's systems, networks, and applications to detect and analyze any suspicious activities or potential threats in real-time, ensuring early identification of risks.
Incident Detection and Response: When a security incident is detected, the SOC responds promptly to contain and mitigate its impact, minimizing potential damage and quickly restoring normal operations.
Utilizing Threat Intelligence: By leveraging both internal and external threat intelligence, the SOC can identify emerging threats and implement proactive defense strategies to stay ahead of potential risks.
Vulnerability Management: SOC teams continuously identify vulnerabilities in systems and infrastructure, assess their severity, and prioritize remediation efforts to prevent exploitation by cyber attackers.
Compliance Management: The SOC ensures the organization adheres to relevant security regulations and industry standards, helping mitigate the risk of penalties and maintaining client and stakeholder trust.
Cyber threats encompass a wide range of risks, including:
Malware: Malicious software, such as viruses, worms, ransomware, and spyware, designed to damage, disrupt, or gain unauthorized access to systems.
Phishing Attacks: Fraudulent attempts to deceive individuals into revealing sensitive information, such as usernames, passwords, and financial details, often via emails or fake websites.
Ransomware: A type of malware that encrypts a victim's files or locks access to critical systems, demanding payment for the decryption key.
Denial of Service (DoS) Attacks: Attacks aimed at overwhelming a system, server, or network with excessive traffic, rendering it inaccessible to users.
SQL Injection: A type of attack that exploits vulnerabilities in a website's database query functionality to gain unauthorized access to data.
Insider Threats: Security risks originating from within the organization, where employees or contractors misuse their access to compromise sensitive information or systems.
Advanced Persistent Threats (APT): Long-term, targeted cyberattacks often orchestrated by sophisticated threat actors, such as nation-states, to infiltrate and maintain unauthorized access to sensitive networks.
Zero-Day Vulnerabilities: Exploits that take advantage of unknown or unpatched vulnerabilities in software or systems, often leaving organizations exposed before a fix is available.
Understanding these diverse threats is crucial for building effective defenses and ensuring cybersecurity resilience.
The SOC leverages a variety of advanced tools to efficiently detect and respond to potential security threats, including:
Intrusion Detection Systems (IDS): These systems monitor network traffic for unusual or suspicious activity, alerting the SOC team to potential breaches and enabling early detection of known threats.
Security Information and Event Management (SIEM) Systems: SIEM platforms aggregate and analyze security data in real time from across an organization’s IT infrastructure, helping the SOC quickly identify, track, and respond to incidents by correlating various events and activities.
Threat Intelligence Platforms: These tools provide up-to-date information on emerging threats, vulnerabilities, and attack tactics, helping the SOC stay ahead of evolving threats and implement proactive defense strategies.
Together, these tools empower SOC teams to detect, analyze, and respond to security incidents promptly and effectively, ensuring continuous protection against a wide range of cyber threats.
When a breach occurs, a Security Operations Center (SOC) follows a well-defined process to effectively manage and mitigate the impact:
1. Identification: The SOC detects the breach by analyzing security alerts, logs, and threat intelligence. This helps them assess the nature and scope of the incident, providing a clear understanding of what has happened.
2. Containment: To prevent further damage, the SOC isolates affected systems or network segments, limiting the spread of the attack and protecting unaffected parts of the network.
3. Eradication: Once the breach is contained, the SOC works to eliminate the root cause, which may involve removing malicious software, addressing vulnerabilities, and patching or repairing compromised systems.
4. Recovery: In the final step, the SOC restores the affected systems and data to normal operations, while continuously monitoring for any signs of re-infection or recurrence, ensuring that the environment remains secure.
This structured approach allows the SOC to handle breaches efficiently, minimizing the impact and ensuring rapid recovery, while also strengthening defenses to prevent future incidents.
Request for More Information
-SOC Certification Syllabus -
Introduction to Security Operations Centers (SOC)
- Overview of SOC functions and structure
- Importance of SOC in cybersecurity operations
Security Frameworks and Compliance
- Understanding regulatory requirements (e.g., GDPR, HIPAA)
- Compliance frameworks and best practices
Threat Detection and Analysis
- Types of cyber threats and attack vectors
- Anomaly detection techniques
- Using threat intelligence to enhance security
Incident Response Process
- Incident response planning and preparation
- Steps in the incident response lifecycle
- Tools and methodologies for effective response
Security Monitoring and Logging
- Setting up monitoring systems and alerts
- Log management and analysis
- Use of Security Information and Event Management (SIEM) systems
Vulnerability Management
- Identifying and assessing vulnerabilities
- Tools for vulnerability scanning
- Remediation strategies
Hands-on Labs and Simulations
- Real-world simulations of security incidents
- Practical exercises in threat detection and response
Emerging Threats and Trends
- Analysis of recent cyber threats and trends
- Future challenges in cybersecurity
Career Development in SOC
- Building a career in cybersecurity
- Resume building and interview preparation
- Networking and professional development opportunities
Capstone Project
- Final project integrating all learned concepts
- Presentation and evaluation of the project
-SOC Certification Job & Salary -

Common tools utilized in a Security Operations Center (SOC) include Security Information and Event Management (SIEM) systems, Intrusion Detection/Prevention Systems (IDS/IPS), firewalls, Endpoint Detection and Response (EDR) systems, and network monitoring tools. These tools work together to detect, analyze, and respond to security threats, ensuring a proactive defense against cyber attacks.
A Security Information and Event Management (SIEM) system collects, consolidates, and analyzes security data from various sources across an organization’s IT infrastructure in real-time. It enables the Security Operations Center (SOC) to quickly identify and respond to potential security incidents by correlating events, detecting anomalies, and providing a comprehensive view of the organization’s security posture. With SIEM’s advanced alerting capabilities and automated workflows, the SOC can efficiently detect, investigate, and mitigate threats, ultimately enhancing incident response speed and reducing potential damage from cyberattacks.
Threat intelligence is the process of gathering, analyzing, and interpreting data about current and potential cyber threats. This information provides organizations with insights into the tactics, techniques, and procedures (TTPs) used by attackers, enabling them to understand the evolving threat landscape. By leveraging threat intelligence, organizations can proactively implement defense measures, such as identifying vulnerabilities, strengthening security protocols, and responding to emerging threats before they result in significant damage. This proactive approach helps to reduce risks, enhance incident response, and improve overall cybersecurity resilience.
Threat intelligence enhances Security Operations Center (SOC) operations by supplying critical insights that inform core processes such as threat detection, incident response, and vulnerability management. By providing detailed information about emerging threats, attack vectors, and adversary behavior, threat intelligence enables SOC teams to:
Proactively Identify Risks: With up-to-date intelligence on threats, SOCs can recognize potential risks before they materialize, allowing for quicker detection and mitigation.
Improve Incident Response: Threat intelligence equips SOC analysts with the context needed to respond to incidents more effectively, including understanding attack patterns and potential impacts.
Strengthen Vulnerability Management: SOC teams can prioritize vulnerabilities based on the latest threat intelligence, addressing the most critical weaknesses before they can be exploited by attackers.
Vulnerability management is a critical process within cybersecurity operations that involves identifying, assessing, and mitigating weaknesses in an organization’s IT infrastructure. This ongoing process includes:
Continuous Monitoring: Regularly scanning systems, networks, and applications to detect potential vulnerabilities or security gaps.
Severity Evaluation: Assessing the identified vulnerabilities to determine their potential impact on the organization, prioritizing them based on risk levels.
Mitigation Strategies: Implementing appropriate solutions to remediate or reduce the risks, such as applying patches, adjusting configurations, or deploying security controls.
By proactively managing vulnerabilities, a Security Operations Center (SOC) can help prevent cyberattacks, reduce exposure to threats, and strengthen the overall security posture of the organization, ensuring critical assets remain protected.
Compliance in cybersecurity refers to an organization's adherence to industry standards, regulations, and legal requirements. It plays a crucial role in avoiding legal penalties, protecting sensitive data, and maintaining customer trust.
In the context of a Security Operations Center (SOC), compliance involves the implementation of security policies and practices that align with established frameworks such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and other regulatory standards. These frameworks set guidelines for the protection and management of sensitive data, ensuring that organizations follow best practices in data privacy and security.
By committing to compliance, a SOC not only ensures that the organization operates within legal boundaries but also strengthens its overall security posture. This proactive approach builds confidence among customers, partners, and stakeholders, demonstrating the organization's dedication to safeguarding sensitive information and upholding regulatory requirements.
SOCs generate a variety of reports to provide valuable insights into security operations. These reports include:
- Incident Reports: Documenting details of security incidents, including the nature of the breach, its impact, the response, and the resolution steps.
- Compliance Reports: Ensuring adherence to regulatory requirements and industry standards, detailing how the organization meets security mandates.
- Threat Analysis Reports: Analyzing and identifying emerging threats, attack vectors, and potential risks, helping to strengthen future defense strategies.
- Executive Summaries: Offering high-level insights into the security posture of the organization, highlighting key incidents, vulnerabilities, and mitigation efforts for senior management.
These reports are essential for continuous monitoring, decision-making, and improving security practices within the organization.
Best practices for Security Operations Centers (SOCs) to ensure effective operations and enhance cybersecurity capabilities include:
Regular Staff Training: Continuously educate SOC personnel on emerging security trends, tools, and attack methods. This ensures that the team is always prepared to handle evolving threats and new cyberattack techniques.
Automated Monitoring Tools: Implement automation to streamline processes such as threat detection, incident response, and data analysis. Automation reduces response time, improves efficiency, and helps SOC teams manage large volumes of security data more effectively.
Up-to-Date Threat Intelligence: Regularly update threat intelligence feeds to stay informed about emerging risks and vulnerabilities. This allows the SOC to take proactive defense measures, anticipating and neutralizing potential threats before they materialize.
Routine Security Audits: Perform regular security audits to evaluate the organization's security posture, identify potential weaknesses, and ensure that all security controls are functioning as intended. These audits also verify compliance with industry regulations and standards.
To further enhance the effectiveness of a Security Operations Center (SOC), several key strategies can be implemented:
Integrating Advanced Analytics: Utilize data analytics, machine learning, and artificial intelligence (AI) to analyze large datasets, detect anomalies, and predict potential security threats more accurately. These technologies help SOC teams identify complex attack patterns and respond to emerging threats in real-time, improving overall threat detection capabilities.
Adopting Automation: Automate routine tasks such as threat detection, incident response, and log analysis to streamline operations. Automation not only speeds up response times but also allows SOC analysts to focus on more critical and complex security challenges, increasing the SOC’s overall efficiency.
Promoting a Strong Security Culture: Foster a culture of security awareness throughout the organization by offering continuous training, promoting collaboration across departments, and encouraging adherence to security best practices. Engaging all employees in cybersecurity efforts ensures that potential risks are identified and addressed more swiftly.
Continuously Updating Processes and Tools: Regularly evaluate and update SOC processes, tools, and technologies to stay ahead of evolving cyber threats. This includes reviewing incident response protocols, upgrading detection systems, and ensuring that the SOC is equipped with the latest security technologies to address new risks and improve overall defense capabilities.
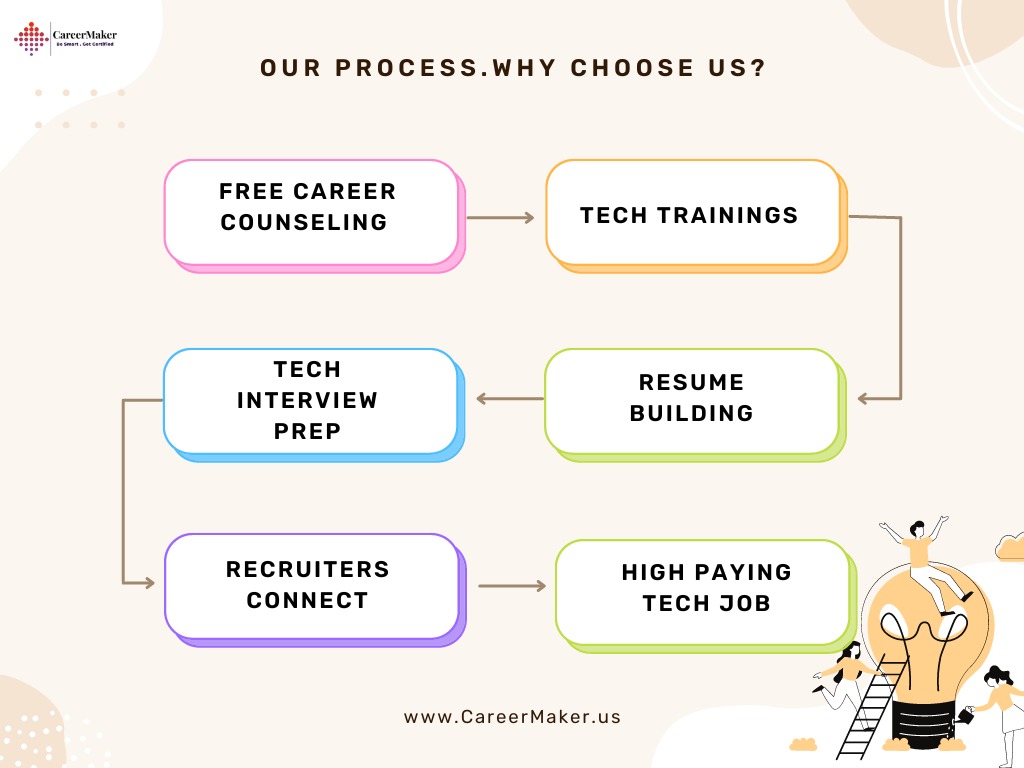
- Benefits Of Choosing CareerMaker Solutions ? -
- Our World-Class CERTIFIED INSTRUCTIOR
As a SOC Analyst at Specialty Solutions, I apply my expertise in cyber threat hunting (CTH) and Splunk Enterprise Security (ES) to monitor, detect, and respond to cyber incidents. I work with a team of cybersecurity professionals to protect the company's network and systems from malicious actors and ensure compliance with industry standards and regulations. I have multiple years of experience in the cybersecurity field, having previously worked as a Security Engineer at SecureTech, where I developed and implemented security solutions and policies. I have also acquired multiple certifications and skills in CTH, Splunk ES, and cybersecurity incident response, which enable me to perform my role effectively and efficiently. I am passionate about cybersecurity and always eager to learn new technologies and techniques to enhance my knowledge and skills
Nim Fon Queenette.
SOC Instructor- Certification Of Course Completion -

- Success Stories -
ARE YOU READY TO TAKE YOUR CYBER SECURITY CAREER TO THE NEXT LEVEL -
Don’t miss the chance to elevate your cybersecurity career with our comprehensive Security Operations Center (SOC) certification training. Enroll today to acquire the critical skills and knowledge needed to defend organizations against the ever-evolving cyber threat landscape.
Contact us now to learn more about our training program, course schedules, and enrollment options. Start your journey toward a rewarding career in cybersecurity today!

- FAQ -
This program is perfect for aspiring SOC analysts, cybersecurity professionals seeking to enhance their expertise, and individuals eager to master the techniques, tools, and methodologies essential for success in today’s dynamic Security Operations Center (SOC) environments. Whether you're just starting or looking to advance your career, this training equips you with the knowledge and hands-on experience needed to thrive in the cybersecurity field.
Participants will engage in real-world scenarios, including simulated cyberattacks and incident response exercises, to apply their skills in a practical setting. Additionally, they will develop Python scripts to automate SOC tasks and analyze security data, honing their hands-on skills crucial for effective SOC operations and improving overall security management.
The program seamlessly blends theoretical knowledge with practical exercises, enabling you to apply what you learn to real-world scenarios. You'll gain hands-on experience with industry-standard tools and technologies, equipping you to effectively address and mitigate complex cybersecurity threats in a professional environment. This combination of theory and practice ensures that you are well-prepared to handle the evolving challenges in cybersecurity and succeed in high-level SOC roles.
The program seamlessly blends theoretical knowledge with practical exercises, enabling you to apply what you learn to real-world scenarios. You'll gain hands-on experience with industry-standard tools and technologies, equipping you to effectively address and mitigate complex cybersecurity threats in a professional environment. This combination of theory and practice ensures that you are well-prepared to handle the evolving challenges in cybersecurity and succeed in high-level SOC roles.
The program seamlessly blends theoretical knowledge with practical exercises, enabling you to apply what you learn to real-world scenarios. You'll gain hands-on experience with industry-standard tools and technologies, equipping you to effectively address and mitigate complex cybersecurity threats in a professional environment. This combination of theory and practice ensures that you are well-prepared to handle the evolving challenges in cybersecurity and succeed in high-level SOC roles.
In this program, you will gain hands-on experience with industry-standard tools such as Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), and Endpoint Detection and Response (EDR) platforms. Additionally, you will master Python programming, enabling you to automate security tasks, streamline processes, and enhance your ability to detect and respond to threats more efficiently. This combination of technical proficiency and automation skills will equip you with the tools needed to excel in a modern Security Operations Center (SOC) environment.
The Master SOC Analyst Training Program equips you with the advanced skills and certification necessary to distinguish yourself in the competitive cybersecurity job market. By mastering Python programming and gaining hands-on experience with critical tools such as SIEM, IDS, and EDR, you’ll be fully prepared to excel in high-level SOC roles. This comprehensive training will not only enhance your technical expertise but also accelerate your career in the ever-growing field of cybersecurity, positioning you as a valuable asset to any organization.


