Security Operations Center (SOC) Training and Certification in Maine
Unlock your career potential with CareerMaker Solutions’ comprehensive SOC Certification in Maine. Our Security Operations Center (SOC) Training in Maine provides practical knowledge and hands-on experience in threat detection, incident response, and cybersecurity management. Designed for both beginners and experienced professionals, our program equips you with the essential skills needed to excel in today’s rapidly evolving security landscape. With expert-led courses and real-world scenarios, you’ll gain the expertise necessary to protect critical digital assets. Enroll today and take the next step in advancing your cybersecurity career!
Years in IT training industry
IT professional Trained
Countries
Bootcamps
- TRUSTED BY -










- SOC COURSE HIGHLIGHTS -

SOC Certification Training Highlights with CareerMaker
Comprehensive Curriculum: Our SOC (Security Operations Center) certification training provides an in-depth, up-to-date curriculum that covers crucial areas like threat detection, incident response, and security monitoring. You’ll be well-prepared for real-world cybersecurity challenges.
Hands-on Experience: Develop practical skills through real-world simulations and hands-on labs, allowing you to manage and mitigate security threats across various environments effectively.
Expert Instructors: Learn from experienced cybersecurity professionals with deep expertise in SOC operations. Their insights and practical guidance will help you succeed in your career.
Flexible Learning Options: Choose from online, in-person, or hybrid learning formats to accommodate your schedule and learning preferences, making it easier to integrate training into your lifestyle.
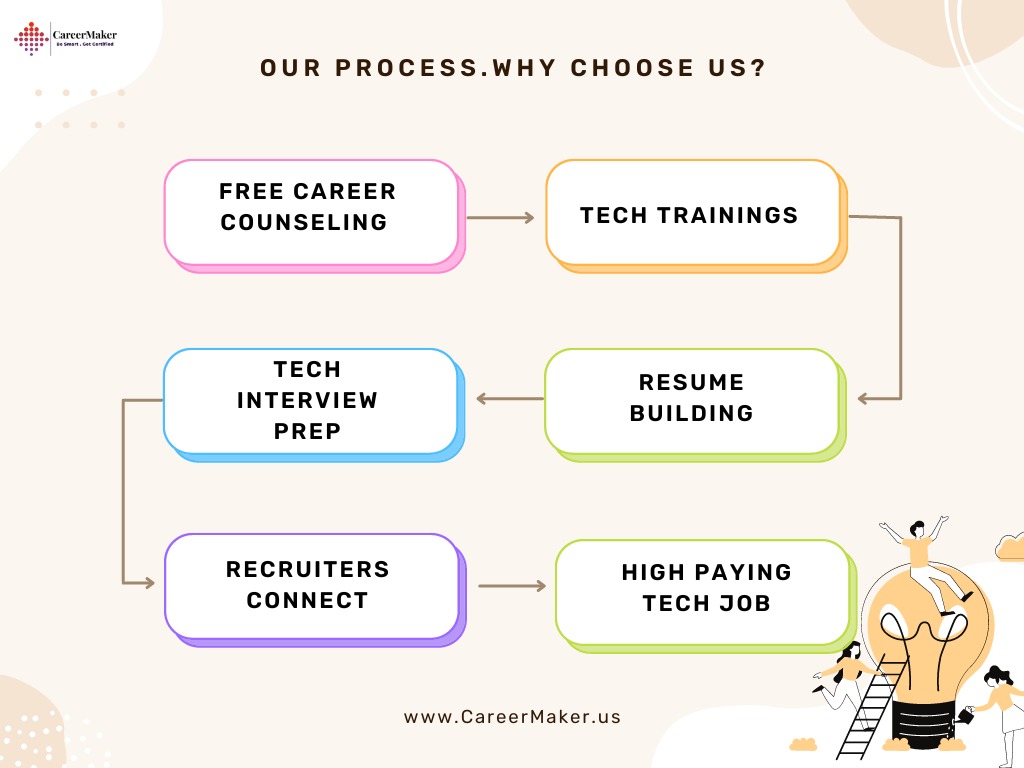
Career Support: Benefit from career guidance, resume-building workshops, and job placement assistance to accelerate your path to a successful cybersecurity career.
Industry-Recognized Certification: Earn a SOC certification recognized by leading organizations in the cybersecurity industry, enhancing your professional credibility and unlocking new job opportunities.
Networking Opportunities: Connect with peers, mentors, and industry experts to expand your professional network and build lasting relationships within the cybersecurity community.
- Upcoming Live BOOTCAMP CALENDAR -
Class Schedule
| 08:00 AM-10:00 AM(EST) | Weekend Evening | October 26 2024 - November 24 2024 | Live Online | $1200 STUDY NOW PAY LATER | INQUIRY NOW |
| 05:00 PM-08:00 PM(CST) | Weekend Evening | October 26 2024 - November 24 2024 | Live Online | $1200 STUDY NOW PAY LATER | INQUIRY NOW |
| 10:00 AM to 06:00PM(CST) | Weekdays | October 07 2024- November 02 2024 | Live Online | $1200 STUDY NOW PAY LATER | INQUIRY NOW |
October 26 2024 To November 24 2024
October 26 2024 To November 24 2024
October 07 2024 To November 02 2024
-Security Operation Center Training Program -
A Security Operations Center (SOC) is a specialized team responsible for managing and addressing an organization's security concerns on both technical and operational fronts. The SOC continuously monitors networks, systems, and applications, detecting potential security threats and responding to incidents in real-time. Its primary goal is to protect the organization's digital assets by proactively identifying vulnerabilities, mitigating risks, and defending against breaches and cyberattacks. Through constant vigilance and swift incident response, the SOC plays a critical role in maintaining the security and integrity of an organization's IT infrastructure.
Continuous Monitoring: The SOC team continuously monitors the organization’s systems, networks, and applications to detect and analyze suspicious activities or potential threats in real time, ensuring early threat identification.
Incident Detection and Response: The SOC swiftly identifies security incidents and responds immediately, containing and mitigating their impact to minimize potential damage to the organization.
Utilizing Threat Intelligence: By integrating both external and internal threat intelligence, the SOC anticipates emerging threats, developing proactive defense strategies to counter potential risks before they escalate.
Vulnerability Management: SOC teams assess and identify vulnerabilities across the organization's systems and infrastructure, prioritize them based on risk, and implement remediation strategies to prevent exploitation by cyber attackers.
Compliance Management: The SOC ensures that the organization adheres to security regulations and industry standards, helping to mitigate the risk of penalties and maintaining trust with clients and stakeholders by securing compliance.
Cyber threats encompass a wide range of risks, including:
Malware: Malicious software designed to harm or disrupt systems, such as viruses, worms, ransomware, and spyware. Malware can infiltrate devices to steal data, damage files, or take control of systems.
Phishing Attacks: Fraudulent attempts, often through email or fake websites, to deceive individuals into revealing sensitive information, such as passwords or credit card numbers, by posing as legitimate entities.
These are just two of the many types of threats that organizations face, highlighting the need for robust cybersecurity measures to safeguard their digital assets.
The SOC leverages a variety of tools to effectively detect and respond to potential threats, including:
Intrusion Detection Systems (IDS): These tools monitor network traffic for suspicious activity and known threats, alerting the SOC team to potential breaches and abnormal behavior patterns.
Security Information and Event Management (SIEM) Systems: SIEM platforms aggregate and analyze security data from various sources across the network in real time, allowing the SOC to quickly identify, track, and respond to security incidents.
Threat Intelligence Platforms: These systems provide up-to-date intelligence on emerging threats, vulnerabilities, and attack patterns, empowering the SOC to implement proactive defense strategies against evolving cyberattacks.
When a breach occurs, a Security Operations Center (SOC) follows a structured process to manage and mitigate the impact:
Identification: The SOC detects the breach by analyzing security alerts, logs, and threat intelligence to determine the nature, scope, and source of the incident.
Containment: To prevent further damage, the SOC isolates affected systems or network segments, limiting the spread of the attack and minimizing its impact on the organization.
Eradication: After containment, the SOC eliminates the root cause of the breach. This may involve removing malware, closing security vulnerabilities, and repairing compromised systems.
Recovery: The SOC restores affected systems and data to normal operation while closely monitoring for signs of re-infection or lingering threats to ensure the breach does not recur.
Request for More Information
-SOC Certification Syllabus -
Introduction to Security Operations Centers (SOC)
- Overview of SOC functions and structure
- Importance of SOC in cybersecurity
Security Frameworks and Compliance
- Understanding regulatory requirements (e.g., GDPR, HIPAA)
- Compliance frameworks and best practices
Threat Detection and Analysis
- Types of cyber threats and attack vectors
- Anomaly detection techniques
- Using threat intelligence to enhance security
Incident Response Process
- Incident response planning and preparation
- Steps in the incident response lifecycle
- Tools and methodologies for effective response
Security Monitoring and Logging
- Setting up monitoring systems and alerts
- Log management and analysis
- Use of Security Information and Event Management (SIEM) systems
Vulnerability Management
- Identifying and assessing vulnerabilities
- Tools for vulnerability scanning
- Remediation strategies
Hands-on Labs and Simulations
- Real-world simulations of security incidents
- Practical exercises in threat detection and response
Emerging Threats and Trends
- Analysis of recent cyber threats and trends
- Future challenges in cybersecurity
Career Development in SOC
- Building a career in cybersecurity
- Resume building and interview preparation
- Networking and professional development opportunities
Capstone Project
- Final project integrating all learned concepts
- Presentation and evaluation of the project
-SOC Certification Job & Salary -

Common tools utilized in a Security Operations Center (SOC) include:
Security Information and Event Management (SIEM) systems: These platforms collect, analyze, and correlate security data from various sources, enabling real-time monitoring and incident detection.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, identifying and preventing unauthorized access or attacks.
Firewalls: Firewalls act as a barrier between trusted and untrusted networks, controlling incoming and outgoing traffic based on security policies to prevent unauthorized access.
Endpoint Detection and Response (EDR) systems: EDR tools monitor and respond to security threats on individual endpoints (e.g., computers, servers) by detecting abnormal behavior or malicious activity.
Network Monitoring Tools: These tools continuously observe network traffic to identify performance issues, security threats, and potential vulnerabilities.
A Security Information and Event Management (SIEM) system collects, aggregates, and analyzes security data from multiple sources in real-time, offering comprehensive visibility into an organization's security posture. It helps the Security Operations Center (SOC) quickly identify potential security incidents by correlating events and logs from various systems, networks, and applications. By centralizing this data, a SIEM system enables faster threat detection and response, allowing the SOC to monitor for unusual activity, investigate incidents, and take immediate action to mitigate risks. This proactive approach enhances an organization's ability to defend against cyberattacks and minimize the impact of security breaches.
Threat intelligence is the process of gathering, analyzing, and interpreting information about current and potential cyber threats. This valuable data provides organizations with a clearer understanding of the threat landscape, including attack tactics, techniques, and procedures (TTPs) used by cybercriminals. By leveraging threat intelligence, organizations can proactively defend against cyberattacks by identifying vulnerabilities, anticipating threats, and implementing appropriate measures to prevent or mitigate potential damage before it occurs. This proactive approach helps strengthen an organization's security posture and enhances its ability to respond to emerging threats.
Threat intelligence plays a crucial role in enhancing Security Operations Center (SOC) operations by informing key processes such as threat detection, incident response, and vulnerability management. By providing actionable insights into both current and emerging threats, threat intelligence enables SOC teams to proactively identify potential risks before they escalate. It allows SOC analysts to detect suspicious activity and potential attacks early, respond more effectively to security incidents, and address vulnerabilities before they can be exploited by cybercriminals. This proactive approach strengthens the overall security posture of an organization, minimizing the risk and impact of cyberattacks.
Vulnerability management is the process of identifying, assessing, and mitigating weaknesses within an organization’s IT infrastructure. This ongoing process involves continuous monitoring for vulnerabilities, evaluating their severity, and implementing appropriate strategies to fix or reduce associated risks. By addressing vulnerabilities, a Security Operations Center (SOC) plays a critical role in preventing potential cyberattacks. SOC teams prioritize and remediate vulnerabilities to reduce the likelihood of exploitation, thereby strengthening the overall security posture of the organization and enhancing its ability to defend against evolving threats.
Compliance ensures that an organization adheres to industry standards, regulations, and legal requirements, helping to avoid legal penalties and maintain customer trust. In the context of a Security Operations Center (SOC), compliance involves implementing security measures that align with frameworks such as GDPR, HIPAA, and other regulatory standards. This ensures that sensitive data is protected, and the organization operates within legal and regulatory boundaries. By committing to compliance, the SOC not only strengthens the organization's security posture but also fosters confidence with stakeholders, demonstrating a commitment to safeguarding data and maintaining ethical business practices.
Security Operations Centers (SOCs) generate a variety of reports that provide valuable insights into an organization’s security landscape. These reports include:
Incident Reports: These documents detail the specifics of security incidents, including the nature of the breach, its impact, response actions taken, and the resolution steps. They help the SOC track the effectiveness of incident management and improve future responses.
Compliance Reports: These reports ensure the organization adheres to regulatory requirements and industry standards. They outline how the organization is meeting security mandates, such as GDPR or HIPAA, helping maintain legal compliance and avoid penalties.
Threat Analysis Reports: These reports analyze and identify emerging threats, attack vectors, and potential risks. They provide actionable insights that help SOC teams strengthen defense strategies and stay ahead of evolving cyber threats.
Executive Summaries: Offering high-level insights into the organization’s overall security posture, these reports highlight key incidents, vulnerabilities, and mitigation efforts for senior management. They are essential for strategic decision-making and resource allocation.
Best practices for Security Operations Centers (SOCs) to ensure effective operations and enhance cybersecurity capabilities include:
Regular Staff Training: Continuously educate SOC personnel on the latest security trends, tools, and attack methods. This ensures that they remain well-equipped to handle evolving threats and are prepared to respond effectively to incidents.
Automated Monitoring Tools: Leverage automation to streamline threat detection, analysis, and incident response. Automation can improve efficiency, reduce response time, and help ensure that security issues are addressed promptly and consistently.
Up-to-Date Threat Intelligence: Regularly update threat intelligence feeds to ensure the SOC is aware of the latest emerging risks, attack techniques, and vulnerabilities. This proactive approach enables the SOC to implement defense measures and respond to potential threats before they cause significant harm.
Routine Security Audits: Conduct frequent security audits and vulnerability assessments to identify weaknesses in systems, evaluate the effectiveness of current security measures, and ensure compliance with industry regulations and standards. Regular audits help uncover potential areas for improvement and reinforce security protocols.
To enhance the effectiveness of Security Operations Centers (SOCs), the following strategies should be adopted:
Integrating Advanced Analytics: Leverage data analytics, machine learning (ML), and artificial intelligence (AI) to detect patterns, identify anomalies, and predict potential threats more accurately and swiftly. These advanced technologies can significantly improve threat detection capabilities and reduce false positives, helping SOC teams focus on critical incidents.
Adopting Automation: Automate routine tasks such as threat detection, incident response, and log analysis. By automating these processes, SOC analysts can devote more time to addressing complex and high-priority issues, leading to improved efficiency and faster response times.
Promoting a Strong Security Culture: Cultivate a security-aware culture throughout the organization by providing ongoing training, encouraging collaboration among teams, and raising awareness about security best practices. When employees at all levels understand the importance of security, they can contribute to a more secure environment.
Continuously Updating Processes and Tools: Regularly review and update SOC processes, tools, and technologies to keep pace with evolving threats. This ensures that the SOC remains agile, adaptive, and capable of detecting and mitigating emerging risks, ultimately strengthening the organization’s cybersecurity posture.
- Benefits Of Choosing CareerMaker Solutions ? -
- Our World-Class CERTIFIED INSTRUCTIOR
As a SOC Analyst at Specialty Solutions, I apply my expertise in cyber threat hunting (CTH) and Splunk Enterprise Security (ES) to monitor, detect, and respond to cyber incidents. I work with a team of cybersecurity professionals to protect the company's network and systems from malicious actors and ensure compliance with industry standards and regulations. I have multiple years of experience in the cybersecurity field, having previously worked as a Security Engineer at SecureTech, where I developed and implemented security solutions and policies. I have also acquired multiple certifications and skills in CTH, Splunk ES, and cybersecurity incident response, which enable me to perform my role effectively and efficiently. I am passionate about cybersecurity and always eager to learn new technologies and techniques to enhance my knowledge and skills
Nim Fon Queenette.
SOC Instructor- Certification Of Course Completion -

- Success Stories -
ARE YOU READY TO TAKE YOUR CYBER SECURITY CAREER TO THE NEXT LEVEL -
Don’t miss the opportunity to advance your cybersecurity career with our comprehensive Security Operations Center (SOC) certification training. Enroll today to acquire the essential skills and knowledge needed to protect organizations from the ever-growing landscape of cyber threats.
Contact us now to learn more about our training program, course schedules, and enrollment options. Start your journey towards a rewarding career in cybersecurity today!

- FAQ -
The Master SOC Analyst Training Program is an advanced course designed to equip cybersecurity professionals with the essential skills to excel in Security Operations Center (SOC) roles. This comprehensive program focuses on developing proficiency in Python for security automation, enhancing threat detection capabilities, and mastering incident response techniques to effectively address evolving cyber threats.
By completing this program, participants will gain the advanced knowledge required to lead SOC operations, automate security tasks, and respond to incidents more efficiently in today’s fast-paced cybersecurity environment.
This program is ideal for aspiring SOC analysts, cybersecurity professionals looking to enhance their skills, and individuals interested in mastering the techniques, tools, and methodologies that are critical for success in modern Security Operations Center (SOC) environments. Whether you're starting your career or advancing to a more specialized role, this training will provide you with the expertise needed to thrive in the fast-evolving cybersecurity landscape.
Python is a versatile and widely-used programming language in SOC environments, offering numerous advantages for Security Operations Center (SOC) professionals. It enables the automation of repetitive tasks, the analysis of large datasets, the development of custom security tools, and the enhancement of threat detection capabilities. These features make Python an essential skill for SOC professionals, allowing them to streamline operations, improve efficiency, and better respond to emerging cyber threats.
Participants will engage in real-world scenarios, including simulated cyberattacks and incident response exercises, to apply their skills in a practical setting. Additionally, they will develop Python scripts to automate SOC tasks and analyze security data, honing the hands-on skills crucial for effective SOC operations. These experiences will improve their ability to respond swiftly to security incidents, enhance threat detection, and optimize overall security management in a SOC environment.
The program combines theoretical knowledge with practical exercises, allowing you to apply learned concepts to real-world scenarios. You will gain hands-on experience with industry-standard tools and technologies, preparing you to address and mitigate complex cybersecurity threats in a professional environment. This blend of theory and practice ensures you're equipped with the skills and confidence to excel in Security Operations Center (SOC) roles and safeguard organizations against evolving cyber risks.
Yes, upon successful completion of the program, you will receive a Master SOC Analyst certification that recognizes your advanced expertise in Security Operations Center (SOC) operations. This certification will highlight your specialized skills in threat detection, incident response, automation, and cybersecurity management, making you a valuable asset to potential employers in the cybersecurity field. With this credential, you'll be well-equipped to pursue advanced roles and take on greater responsibilities in securing digital environments.
While prior experience in cybersecurity or programming is advantageous, it is not required. The program is designed to accommodate both beginners and experienced professionals. For those new to the field, it offers a solid foundation in SOC operations, while for seasoned professionals, it provides advanced knowledge and practical skills to refine and expand expertise. This inclusive structure ensures that every participant, regardless of their background, can gain valuable insights and hands-on experience to excel in cybersecurity roles.
You will gain expertise in using industry-standard tools such as Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), and Endpoint Detection and Response (EDR) platforms. In addition, you will master Python programming to automate security tasks, streamline operations, and enhance threat detection capabilities, ensuring you are well-equipped to handle complex security challenges in SOC environments. This combination of hands-on experience with cutting-edge tools and programming skills will significantly elevate your ability to protect organizations from evolving cyber threats.
The Master SOC Analyst Training Program equips you with the advanced skills and certification necessary to distinguish yourself in the competitive cybersecurity job market. By mastering Python programming and gaining hands-on experience with critical tools such as SIEM systems, IDS, and EDR platforms, you'll be fully prepared to excel in high-level SOC roles. This program will not only enhance your technical expertise but also accelerate your career in cybersecurity, empowering you to effectively address complex threats and become a key player in protecting organizations from cyber risks.


