Security Operations Center Training & Certifications in Colorado
Unlock your career potential with CareerMaker Solutions’ comprehensive SOC Training Colorado and Security Operations Center Colorado programs. Whether you’re in Colorado or Alabama, our Security Operations Center (SOC) Alabama and SOC Colorado training offer practical knowledge and hands-on experience in threat detection, incident response, and cybersecurity management. Designed for both beginners and experienced professionals, our courses provide essential skills to thrive in today’s evolving security landscape. With expert-led instruction and real-world scenarios, you’ll gain the expertise needed to excel in cybersecurity and protect critical digital assets. Enroll today and take the next step in advancing your cybersecurity career!
Years in IT training industry
IT professional Trained
Countries
Bootcamps
- TRUSTED BY -










- SOC COURSE HIGHLIGHTS -

SOC Certification Training Highlights with CareerMaker:
Comprehensive Curriculum: Our SOC certification program covers key areas such as threat detection, incident response, security monitoring, and more, providing you with up-to-date and in-depth knowledge of SOC operations.
Hands-on Experience: Gain practical experience through real-world simulations and interactive labs, equipping you to efficiently manage and mitigate security threats in diverse environments.
Expert Instructors: Learn from experienced cybersecurity professionals with extensive SOC backgrounds, offering valuable insights and practical guidance to help you thrive in your career.
Flexible Learning Options: Choose from online, in-person, or hybrid learning formats, providing you with the flexibility to learn at your own pace and according to your personal schedule.
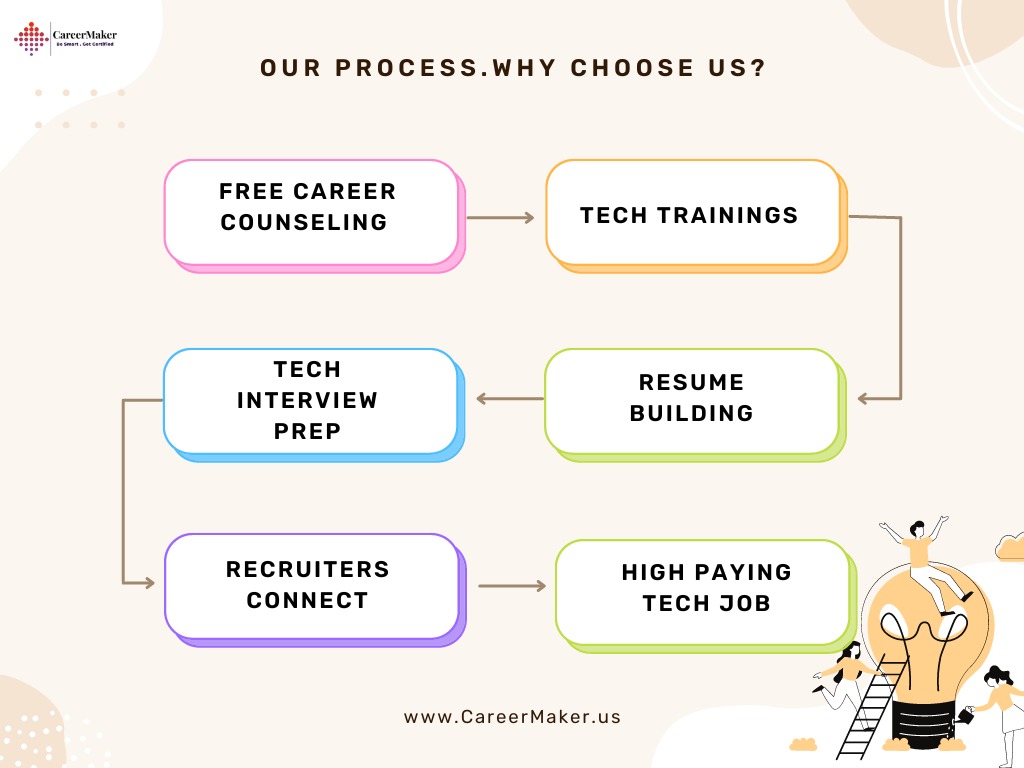
Career Support: Benefit from personalized career coaching, resume workshops, and job placement assistance to fast-track your journey toward a successful cybersecurity career.
Industry-Recognized Certification: Earn a certification that is highly regarded by top organizations in cybersecurity, enhancing your professional credibility and career prospects.
Networking Opportunities: Connect with peers, mentors, and industry leaders through our platform, helping you build a strong professional network within the cybersecurity community
- Upcoming Live BOOTCAMP CALENDAR -
Class Schedule
| 08:00 AM-10:00 AM(EST) | Weekend Evening | October 26 2024 - November 24 2024 | Live Online | $1200 STUDY NOW PAY LATER | INQUIRY NOW |
| 05:00 PM-08:00 PM(CST) | Weekend Evening | October 26 2024 - November 24 2024 | Live Online | $1200 STUDY NOW PAY LATER | INQUIRY NOW |
| 10:00 AM to 06:00PM(CST) | Weekdays | October 07 2024- November 02 2024 | Live Online | $1200 STUDY NOW PAY LATER | INQUIRY NOW |
October 26 2024 To November 24 2024
October 26 2024 To November 24 2024
October 07 2024 To November 02 2024
-Security Operation Center Training Program -
A Security Operations Center (SOC) is a dedicated team that manages and addresses an organization’s security needs both technically and operationally. Its primary role is to continuously monitor, detect, and respond to security threats and incidents in real-time, safeguarding the organization’s digital assets from potential breaches or cyberattacks.
The core functions of a Security Operations Center (SOC) include continuous system monitoring, detecting and responding to security incidents, leveraging threat intelligence, managing vulnerabilities, and ensuring compliance with industry security regulations. These efforts collectively help protect the organization from cyber threats and maintain security integrity.
Cyber threats include a wide range of risks, such as malware, phishing attacks, ransomware, Distributed Denial of Service (DDoS) attacks, insider threats, and advanced persistent threats (APTs). Each of these poses significant danger to an organization's security, requiring vigilant monitoring and response to mitigate potential damage.
A SOC utilizes various tools, such as Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM) systems, and threat intelligence platforms, to effectively detect anomalies and identify potential security threats in real-time. These tools help streamline monitoring and incident response efforts.
In response to a breach, a SOC follows a structured process: first, it identifies the scope of the breach, then contains it to prevent further damage. Next, it eradicates the root cause of the breach, and finally, recovers affected systems and data to restore normal operations.
Request for More Information
-SOC Certification Syllabus -
SOC Programming Syllabus
Introduction to Security Operations Centers (SOC)
- Overview of SOC functions and structure
- The importance of SOC in cybersecurity
Security Frameworks and Compliance
- Understanding regulatory requirements (e.g., GDPR, HIPAA)
- Compliance frameworks and best practices
Threat Detection and Analysis
- Types of cyber threats and attack vectors
- Anomaly detection techniques
- Enhancing security using threat intelligence
Incident Response Process
- Incident response planning and preparation
- Steps in the incident response lifecycle
- Tools and methodologies for effective incident response
Security Monitoring and Logging
- Setting up monitoring systems and alerts
- Log management and analysis
- Utilizing Security Information and Event Management (SIEM) systems
Vulnerability Management
- Identifying and assessing vulnerabilities
- Vulnerability scanning tools
- Remediation strategies
Hands-on Labs and Simulations
- Real-world simulations of security incidents
- Practical exercises in threat detection and response
Emerging Threats and Trends
- Analysis of recent cyber threats and trends
- Future challenges in cybersecurity
Career Development in SOC
- Building a career in cybersecurity
- Resume building and interview preparation
- Networking and professional development opportunities
Capstone Project
- Final project integrating all learned concepts
- Presentation and evaluation of the project
-SOC Certification Job & Salary -

Common tools utilized in a Security Operations Center (SOC) include Security Information and Event Management (SIEM) systems, Intrusion Detection and Prevention Systems (IDS/IPS), firewalls, Endpoint Detection and Response (EDR) systems, and network monitoring solutions. These tools help detect, analyze, and respond to security threats in real time, ensuring comprehensive protection of the organization’s digital assets.
A Security Information and Event Management (SIEM) system collects and analyzes security data from various sources in real time. This enables the Security Operations Center (SOC) to quickly identify and respond to potential security incidents, providing enhanced visibility and faster threat detection across the network.
Threat intelligence is the process of gathering and analyzing data on current and emerging cyber threats. By understanding these risks, organizations can proactively strengthen their defenses, anticipate potential attacks, and make informed decisions to protect their systems and data.
Threat intelligence enhances SOC operations by providing actionable insights that inform threat detection, incident response, and vulnerability management. It helps SOC teams identify emerging threats, improve response strategies, and prioritize vulnerabilities, enabling more proactive and effective cybersecurity measures.
Vulnerability management involves identifying, assessing, and addressing weaknesses in an organization's IT infrastructure. By regularly scanning for vulnerabilities and implementing appropriate remediation strategies, organizations can reduce their exposure to cyber threats and strengthen their overall security posture.
Compliance ensures that an organization adheres to industry standards and regulations, helping to mitigate legal risks, avoid penalties, and build trust with customers. By following best practices and staying up to date with evolving laws, organizations can safeguard their operations and reputation in the cybersecurity landscape.
SOCs generate various reports to support their operations, including incident reports detailing security events, compliance reports to ensure regulatory adherence, threat analysis reports to identify emerging risks, and executive summaries that provide high-level insights for decision-makers and stakeholders. These reports are essential for monitoring performance, ensuring compliance, and guiding future strategies.
Best practices for SOCs involve regularly training staff to stay ahead of evolving threats, using automated monitoring tools to streamline threat detection, maintaining up-to-date threat intelligence for proactive defense, and performing regular security audits to identify vulnerabilities and ensure compliance with industry standards.
A SOC can improve its effectiveness by integrating advanced analytics for better threat detection, adopting automation to increase efficiency, fostering a strong security culture across the organization, and consistently updating processes and tools to stay ahead of emerging cyber threats.
- Benefits Of Choosing CareerMaker Solutions ? -
- Our World-Class CERTIFIED INSTRUCTIOR
As a SOC Analyst at Specialty Solutions, I apply my expertise in cyber threat hunting (CTH) and Splunk Enterprise Security (ES) to monitor, detect, and respond to cyber incidents. I work with a team of cybersecurity professionals to protect the company's network and systems from malicious actors and ensure compliance with industry standards and regulations. I have multiple years of experience in the cybersecurity field, having previously worked as a Security Engineer at SecureTech, where I developed and implemented security solutions and policies. I have also acquired multiple certifications and skills in CTH, Splunk ES, and cybersecurity incident response, which enable me to perform my role effectively and efficiently. I am passionate about cybersecurity and always eager to learn new technologies and techniques to enhance my knowledge and skills
Nim Fon Queenette.
SOC Instructor- Certification Of Course Completion -

- Success Stories -
ARE YOU READY TO TAKE YOUR CYBER SECURITY CAREER TO THE NEXT LEVEL -
Unlock your potential in the cybersecurity field with our comprehensive SOC Certification Training. Gain the expertise to protect organizations from evolving cyber threats.
Contact us today to learn more about our program, flexible schedules, and enrollment options. Start your journey toward a rewarding cybersecurity career now!

- FAQ -
The Master SOC Analyst Training Program is an advanced course tailored to equip cybersecurity professionals with the critical skills needed to thrive in Security Operations Center (SOC) roles. This program focuses on mastering Python for security automation, enhancing threat detection, and enabling efficient incident response to strengthen your SOC capabilities.
This program is ideal for aspiring SOC analysts, experienced cybersecurity professionals looking to refine their expertise, and anyone eager to master the tools and techniques necessary for excelling in modern Security Operations Center (SOC) operations.
Python is a powerful and versatile programming language commonly used in SOC environments. It helps automate tasks, analyze large datasets, develop custom security tools, and enhance threat detection capabilities, making it an essential tool for modern cybersecurity operations.
Participants will engage in real-world scenarios, including simulated cyber attacks and incident response exercises. They will also develop Python scripts to automate SOC tasks and analyze security data, honing practical skills necessary for efficient threat detection and incident management in SOC operations.
The program blends theoretical knowledge with practical exercises, enabling you to apply learned concepts to real-world situations. You’ll gain experience with industry-standard tools and technologies, equipping you to tackle complex cybersecurity threats in a professional environment.
Upon successful completion of the program, you will receive a certification that validates your expertise as a Master SOC Analyst. This certification demonstrates your advanced skills and proficiency in SOC operations, boosting your credibility and opening doors to higher-level cybersecurity roles.
While prior experience in cybersecurity or programming can be helpful, it is not required. The program is designed to accommodate both beginners and experienced professionals, providing a structured learning path to enhance skills and knowledge for individuals at all levels.
You will gain proficiency in using industry-standard tools like Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), and Endpoint Detection and Response (EDR) platforms, while also mastering Python programming to automate tasks and enhance threat detection capabilities in SOC environments.
The Master SOC Analyst Training Program provides you with advanced skills and certification to distinguish yourself in the cybersecurity field. By mastering Python and gaining hands-on experience, you'll be well-prepared to take on high-level SOC roles and accelerate your career in cybersecurity.


