CompTIA CySA+ Certification Training
Are you passionate about cybersecurity and seeking to take your career to new heights? At CareerMaker, we offer comprehensive CompTIA CySA+ certification training designed to equip you with advanced cybersecurity skills and propel your professional growth. Our training program is designed to provide you with the knowledge and practical expertise required to excel in the ever-evolving field of cybersecurity.
As an IT workforce certification, CompTIA Cybersecurity Analyst (CySA+) uses behavioral analytics on networks and devices to prevent, identify, and counteract cybersecurity threats through ongoing security monitoring. The only intermediate, high-stakes cybersecurity analyst certification that includes multiple-choice and performance-based questions.
4.2/5
![]() 4.8/5
4.8/5 ![]() 4.6/5
4.6/5
Years in IT training industry
IT professional Trained
Countries
Bootcamps
- TRUSTED BY -










- CompTIA CYSA+ COURSE HIGHLIGHTS -

- 5-day CompTIA Cybersecurity Analyst Certification Training conducted by instructors
- To further prepare for the training get free access to the CompTIA Cybersecurity Analyst course preview
- Courseware for CompTIA Accredited Cybersecurity Analysts created by SMEs
- Utilize CompTIA templates and case studies from several industry sectors to gain practical experience
- Certificate of completion for the well-known CompTIA Cybersecurity Analyst training programme
- Worldwide seasoned CompTIA educators with a variety of industry Utilize CompTIA templates and case studies from several industry sectors to gain practical experience
- Training for CompTIA CySA+ is offered in more than 100 places worldwide
- Upcoming Live BOOTCAMP CALENDAR -
Schedule of Classes
| 07:00 AM-11:00 AM(CST) | Weekend Morning | FEB 24 2024- MARCH 24 2024 | Live Online | ENROLL NOW | INQUIRY NOW |
| 07:00 PM-11:00 PM(CST) | Weekend Evening | FEB 24 2024- MARCH 24 2024 | Live Online | ENROLL NOW | INQUIRY NOW |
| 10:00 AM to 06:00PM(CST) | Weekdays | FEB 26 2024- MARCH 01 2024 | Live Online | ENROLL NOW | INQUIRY NOW |
August 19 2023- September 17 2023
August 19 2023- September 17 2023
August 21 2023- August 25 2023
- CompTIA CYSA+ COURSE DESCRIPTION -
The CompTIA Cybersecurity Analyst (CySA+) course provides a comprehensive overview of advanced cybersecurity concepts and skills, focusing on threat detection, analysis, and response. This certification equips professionals with the expertise needed to protect organizations from evolving cyber threats.
The CompTIA CySA+ course prepares professionals to take on roles such as cybersecurity analyst, security operations center (SOC) analyst, and security consultant. The certification validates your ability to proactively defend against cyber threats and contribute to the overall security posture of an organization. Through hands-on labs and real-world scenarios, the course equips you with practical skills to analyze and respond to various security incidents effectively
- Cybersecurity Analysts
- Security Operations Center (SOC) Analysts
- IT Professionals transitioning to cybersecurity roles
- Network Administrators
- Incident Responders
- Security Consultants
- Security Engineers
- Compliance Analysts
- Threat Intelligence Analysts
- Vulnerability Analysts
- Basic knowledge of computer hardware, software, and operating systems.
- Fundamental understanding of networking concepts and protocols.
- Familiarity with cybersecurity fundamentals and concepts.
- Experience in IT or cybersecurity roles is recommended but not mandatory.
- CompTIA Network+ or CompTIA Security+ certification (recommended, but not required).
- Strong analytical and problem-solving skills to effectively analyze and respond to security incidents.
- Proficiency in interpreting security-related data and logs.
- Understanding of risk management and compliance principles.
- Knowledge of threat detection and response techniques.
- Ability to communicate security issues and recommendations clearly to technical and non-technical stakeholders.
Exam Codes | CS0-002 | CS0-003 |
Launch Date | April 21, 2020 | June 6, 2023 |
Exam Description | The CompTIA Cybersecurity Analyst (CySA+) certification verifies that successful candidates have the knowledge and skills required to leverage intelligence and threat detection techniques, analyze and interpret data, identify and address vulnerabilities, suggest preventative measures, and effectively respond to and recover from incidents. | The CompTIA Cybersecurity Analyst (CySA+) certification verifies that successful candidates have the knowledge and skills required to detect and analyze indicators of malicious activity, understand threat intelligence and threat management, respond to attacks and vulnerabilities, perform incident response, and report and communicate related activity. |
Number of Questions | Maximum of 85 questions | |
Type of Questions | Multiple choice and performance-based | |
Length of Test | 165 minutes | |
Passing Score | 750 (on a scale of 100-900) | |
Recommended Experience | Network+, Security+ or equivalent knowledge. Minimum of 4 years of hands-on information security or related experience. | Network+, Security+ or equivalent knowledge. Minimum of 4 years of hands-on experience as an incident response analyst or security operations center (SOC) analyst, or equivalent experience. |
Languages | English, Japanese | English, with Japanese, Portuguese and Spanish to follow |
Retirement | December 5, 2023 – English, Japanese to follow. | TBD – Usually three years after launch |
$392 is the exam fee for compTIA CYSA+
750 (on a scale of 100-900)
- 1.0 Security Operations 33%
- 2.0 Vulnerability Management 30%
- 3.0 Incident Response and Management 20%
- 4.0 Reporting and Communication 17%
- Total 100%
The CompTIA CySA+ certification is valid for a period of 3 years from the date of successful certification. To maintain the certification's validity and demonstrate your up-to-date skills in the ever-changing cybersecurity landscape, you have the option to renew your CompTIA CySA+ certification by completing continuing education activities or retaking the latest version of the certification exam. The renewal process helps ensure that certified professionals stay current with the latest cybersecurity practices and knowledge.
compTIA CYSA+ syallabus
Threat Management 27% | |
Given a scenario, apply environmental reconnaissance techniques using appropriate tools and processes. | 1. Procedures/common tasks
2. Variables
3. Tools
|
Given a scenario, analyze the results of a network reconnaissance. | 1. Point-in-time data analysis
2. Data correlation and analytics
3. Data output
4. Tools
|
Given a network-based threat, implement or recommend the appropriate response and countermeasure. | 1. Network segmentation
2. Honeypot
6. Hardening
7. Network Access Control (NAC)
|
Explain the purpose of practices used to secure a corporate environment. | 1. Penetration testing
2. Reverse engineering
3. Training and exercises
4. Risk evaluation
|
Vulnerability Management 26% | |
Given a scenario, implement an information security vulnerability management process. | 1. Identification of requirements
2. Establish scanning frequency
3. Configure tools to perform scans according to specification
4. Execute scanning
6. Remediation
7. Ongoing scanning and continuous monitoring |
Given a scenario, analyze the output resulting from a vulnerability scan. | 1. Analyze reports from a vulnerability scan
2. Validate results and correlate other data points
|
Compare and contrast common vulnerabilities found in the following targets within an organization. | 1. Servers
6. Mobile devices |
Cyber Incident Response 23% | |
Given a scenario, distinguish threat data or behavior to determine the impact of an incident. | 1. Threat classification
2. Factors contributing to incident severity and prioritization
|
Given a scenario, prepare a toolkit and use appropriate forensics tools during an investigation. | 1. Forensics kit
2. Forensic investigation suite
|
Explain the importance of communication during the incident response process. | 1. Stakeholders
2. Purpose of communication processes
3. Role-based responsibilities
|
Given a scenario, analyze common symptoms to select the best course of action to support incident response. | 1. Common network-related symptoms
2. Common host-related symptoms
3. Common application-related symptoms
|
Summarize the incident recovery and post-incident response process. | 1. Containment techniques
2. Eradication techniques
3. Validation
4. Corrective actions
5. Incident summary report |
Security Architecture and Tool Sets 24% | |
Explain the relationship between frameworks, common policies, controls, and procedures. | 1. Regulatory compliance
3. Policies
4. Controls
5. Procedures
6. Verifications and quality control
|
Given a scenario, use data to recommend remediation of security issues related to identity and access management. | 1. Security issues associated with context-based authentication
2. Security issues associated with identities
3. Security issues associated with identity repositories
4. Security issues associated with federation and single sign-on
5. Exploits
|
Given a scenario, review security architecture and make recommendations to implement compensating controls. | 1. Security data analytics
2. Manual review
3. Defense in depth
|
Given a scenario, use application security best practices while participating in the Software Development Life Cycle (SDLC). | 1. Best practices during software development
2. Secure coding best practices
|
Compare and contrast the general purpose and reasons for using various cybersecurity tools and technologies. | 1. Preventative
2. Collective
3. Analytical
4. Exploit
5. Forensics
|
Request for more Information
- CompTIA CYSA+ COURSE SYLLABUS -
- The CompTia CYSA+ certification focuses on intermediate levels of cyber security and incident detection for Defence.
- Applying firewalls and an analytics-based strategy in an organization
- To discover threats, risks, security alerts, and vulnerabilities in an organization do data analysis and interpret the findings.
- Establishing, implementing, and utilizing threat detection tools and verifying knowledge and abilities in intermediate security.
- Information on Security Architects, Cyber Incident Response, and Threat and Vulnerability Management.
- Describing the connections between various frameworks and policies, as well as comprehending the controls and processes.
- CompTIA CYSA+ JOBS & SALARY -
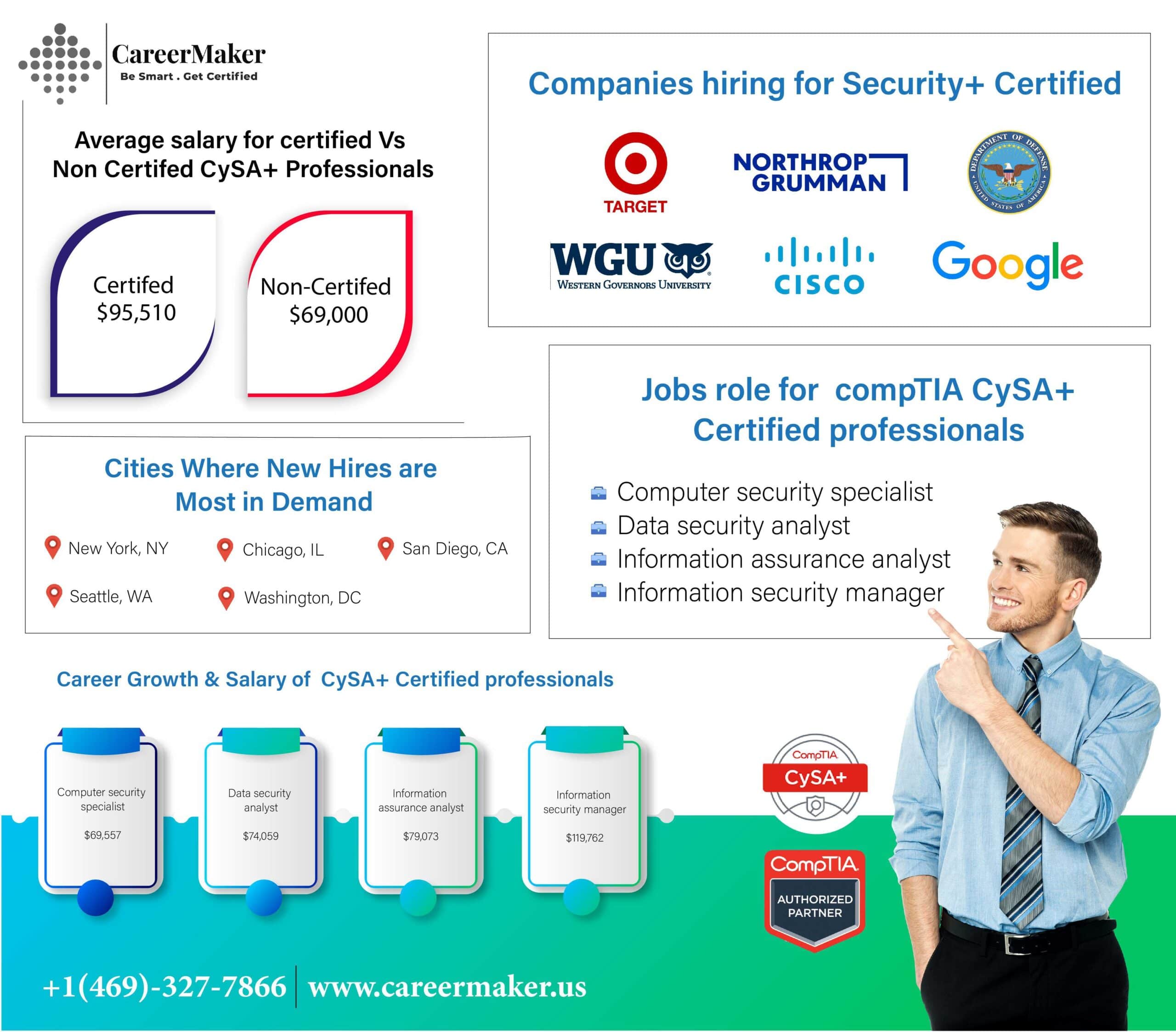
CompTIA CySA+ opens doors to roles such as Cybersecurity Analyst, SOC Analyst, Threat Intelligence Analyst, and Incident Responder.
CompTIA CySA+ is highly regarded in industries with strong cybersecurity needs, such as finance, healthcare, government, and technology.
CompTIA CySA+ certified professionals can earn an average annual salary ranging from $60,000 to $100,000, depending on experience and location.
Yes, CompTIA CySA+ certification can potentially lead to higher-paying cybersecurity roles compared to non-certified positions.
Yes, benefits include increased employability, enhanced cybersecurity skills, and the ability to contribute to organizational security strategies.
Yes, CompTIA CySA+ is widely recognized and respected by employers and recruiters in the cybersecurity field.
While not always a strict requirement, CompTIA CySA+ can greatly improve your chances of being considered for cybersecurity roles.
Yes, CompTIA CySA+ can serve as a valuable credential for IT professionals looking to transition into cybersecurity positions.
Yes, CompTIA CySA+ can pave the way for more advanced roles such as Security Analyst, Security Engineer, and Security Consultant.
CompTIA CySA+ certified professionals possess the skills to detect and respond to cybersecurity threats, helping organizations safeguard their digital assets and data.
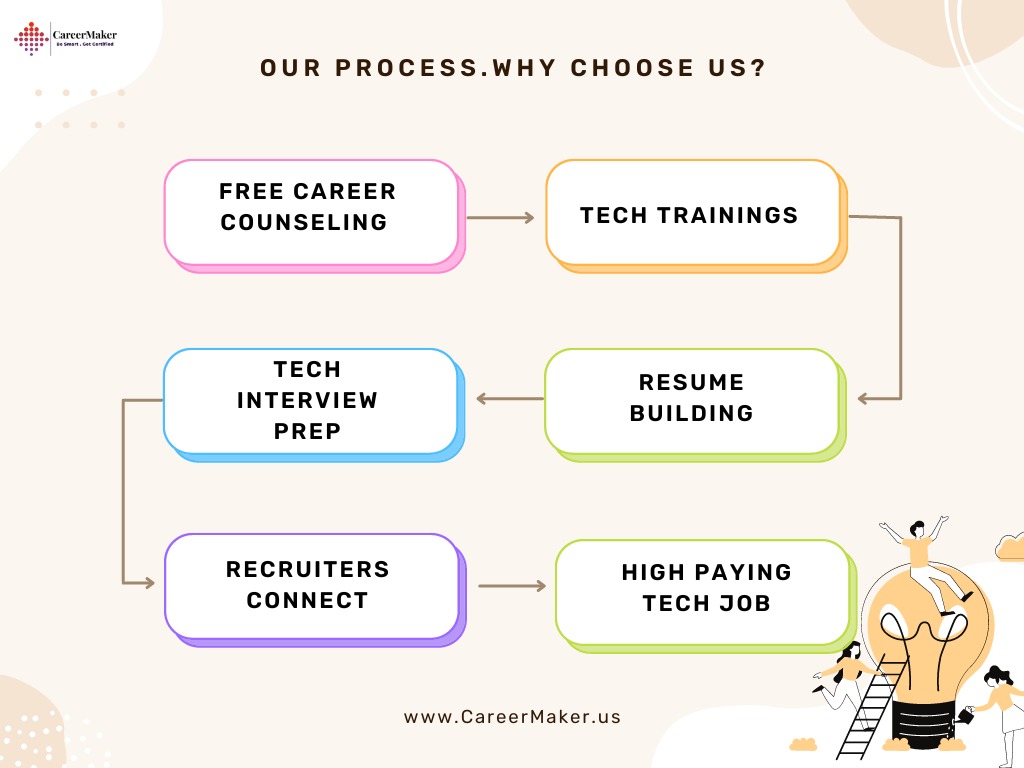
- Benefits Of Choosing CareerMaker Solutions ? -
- Our World-Class CERTIFIED INSTRUCTIOR -
- Certification of Course Completion -

- Success Stories -
Elevate Your Cybersecurity Career Today -
Don’t miss out on the opportunity to enhance your cybersecurity career with our comprehensive CompTIA CySA+ certification training. Join us today and gain the knowledge and skills needed to thrive in the ever-changing world of cybersecurity.
Call Us Today to learn more about our training program, course schedules, and enrollment options. Start your journey towards a successful cybersecurity career today!

- FAQ -
CompTIA CySA+ certification validates skills in threat detection, analysis, and response, making professionals proficient in cybersecurity operations.
The course covers threat management, vulnerability management, security operations, compliance, incident response, and more.
No, CompTIA CySA+ is an intermediate-level certification designed for professionals with foundational cybersecurity knowledge.
Benefits include enhanced employability, higher earning potential, and the ability to contribute to an organization's cybersecurity posture.
While not mandatory, practical experience in cybersecurity operations enhances understanding of course concepts.
CompTIA CySA+ opens doors to roles like Cybersecurity Analyst, SOC Analyst, Threat Intelligence Analyst, and Incident Responder.
The duration varies based on individual pace, but most candidates complete the training within a few months.
Yes, you can find online training courses to prepare for the CompTIA CySA+ certification.
CompTIA CySA+ certified professionals can earn an average annual salary ranging from $60,000 to $100,000, depending on factors like experience and location.
Yes, as cybersecurity threats continue to evolve, the demand for skilled professionals with CompTIA CySA+ expertise is on the rise.
ou'll gain skills in threat detection, vulnerability assessment, incident response, and security operations.
Yes, CompTIA CySA+ is widely recognized and respected in the cybersecurity industry.
Yes, CompTIA CySA+ can provide a solid foundation for transitioning from other IT roles to cybersecurity.
Yes, there are study guides, practice exams, and official CompTIA resources to help you prepare for the exam.
CompTIA CySA+ primarily focuses on defensive cybersecurity, emphasizing threat detection and incident response.
CompTIA CySA+ certification needs to be renewed every three years through continuing education or retaking the latest exam version.
Yes, CompTIA CySA+ is designed for professionals with some experience in cybersecurity operations.
While not mandatory, CompTIA Network+ or CompTIA Security+ certifications can provide a helpful foundation.
Yes, CompTIA CySA+ certification is often recognized and accepted for cybersecurity roles in government organizations.
Yes, CompTIA CySA+ can pave the way for more advanced roles such as Security Analyst, Security Engineer, and Consultant.
Industries such as finance, healthcare, government, and technology highly value CompTIA CySA+ certified professionals.
While not a primary focus, CompTIA CySA+ may touch on basic cloud security concepts within its broader curriculum.
Yes, CompTIA CySA+ can provide a competitive edge and increase job prospects when applying for cybersecurity positions.
Yes, CompTIA CySA+ is well-regarded by employers and recruiters looking for skilled cybersecurity professionals.
CompTIA CySA+ certified professionals are equipped to proactively detect, analyze, and respond to cybersecurity threats, helping safeguard digital assets and data

