Certified Ethical Hacking Certification & Training (CEH) V12
Are you passionate about cybersecurity and intrigued by ethical hacking? At CareerMaker, we offer a comprehensive certified ethical hacking training program designed to help you become a skilled and certified ethical hacker. Our training program is specifically tailored to provide you with the knowledge and practical expertise required to excel in the exciting world of ethical hacking.
The Certified Ethical Hacking Certification training, now in its 12th edition, combines thorough instruction, practical learning laboratories, engagement-based practise cyber ranges, certification examinations, cyber competitions, and chances for continuing learning into one comprehensive programme: Learn, Get certified, Get involved, Compete.
Years in IT training industry
IT professional Trained
Countries
Bootcamps
- TRUSTED BY -










- CEH v12 Certification COURSE HIGHLIGHTS -

- Expert instructors give a well-known CEH course with certification training.
- Learn everything there is to know about the most widely used information security standards.
- Become a Certified Ethical Hacker to advance in your job.
- To assist you to pass your CEH certification exam, expert cybersecurity lecturers and practical lab sessions are available.
- Get in touch with other IT security experts from other industry sectors to learn more about security breaches
- Upcoming Live BOOTCAMP CALENDAR -
Schedule of Classes
| 07:00 AM-11:00 AM(CST) | Weekend Morning | FEB 24 2024- MARCH 24 2024 | Live Online | ENROLL NOW | INQUIRY NOW |
| 07:00 PM-11:00 PM(CST) | Weekend Evening | FEB 24 2024- MARCH 24 2024 | Live Online | ENROLL NOW | INQUIRY NOW |
| 10:00 AM to 06:00PM(CST) | Weekdays | FEB 26 2024- MARCH 01 2024 | Live Online | ENROLL NOW | INQUIRY NOW |
August 26 2023- September 24 2023
August 26 2023- September 24 2023
August 28 2023- September 01 2023
-CEH v12 Certification Course Description -
The Certified Ethical Hacker (CEH) course offers participants comprehensive insights into ethical hacking techniques and practices. This course equips individuals with the knowledge and skills required to identify vulnerabilities, assess potential risks, and secure systems and networks proactively.
This course is ideal for individuals aspiring to become ethical hackers, penetration testers, security analysts, network administrators, and other professionals interested in enhancing their cybersecurity skills. It is also suitable for those responsible for securing organizational IT infrastructure
- Aspiring Ethical Hackers
- Cybersecurity Professionals
- Network Administrators
- Information Security Officers
- IT Managers and Directors
- System Administrators
- Penetration Testers
- Security Researchers
- Technology Enthusiasts
- Graduates and Students
- Career Changers
- Basic understanding of networking concepts
- Familiarity with operating systems
- Knowledge of cybersecurity fundamentals (beneficial but not mandatory)
- Exam Title: Certified Ethical Hacker (CEH)
- Exam Format: Multiple-choice questions
- Number of Questions: Approximately 125 questions
- Exam Duration: 4 hours
- Passing Score: Typically, a scaled score of 70% or higher
Exam Delivery: Proctored exam delivered in-person or remotely
The Certified Ethical Hacker exam cost is $1199.
The exam consists of 125 multiple-choice questions to be completed in four hours with a passing score of 70%
- Exam Topics: Covers various domains such as Ethical Hacking, Footprinting and Reconnaissance, Scanning Networks, Enumeration, System Hacking, Malware Threats, Sniffing, Social Engineering, Denial of Service, Session Hijacking, Web Application Security, and more.
- Practical Exam: Candidates also have the option to take a separate practical exam to demonstrate real-world skills
- Certification Validity: The CEH certification is valid for three years from the date of certification achievement.
- Renewal Requirement: To maintain the CEH certification, certified professionals are required to earn and submit a minimum of 120 Continuing Professional Education (CPE) credits within the three-year renewal cycle.
Request for more Information
-CEH v12 Certification Syllabus -
Introduction to Ethical Hacking
- Elements of Information Security
- Cyber Kill Chain Methodology
- MITRE ATT&CK Framework
- Hacker Classes
- Ethical Hacking
Foot Printing and Reconnaissance
- Footprinting
- Advanced Google Hacking Techniques
- Deep and Dark Web Footprinting
- Competitive Intelligence Gathering
- Website Footprinting
Scanning Networks
- Network Scanning
- Host Discovery Techniques
- Port Scanning Techniques
- Service Version Discovery
- OS Discovery
- Banner Grabbing
Vulnerability Analysis
- Enumeration
- NetBIOS Enumeration
- SNMP Enumeration
- LDAP Enumeration
- NTP Enumeration
- NFS Enumeration
- SMTP Enumeration
- DNS Cache Snooping
Enumeration
- NetBIOS Enumeration
- SNMP Enumeration
- LDAP Enumeration
- NTP Enumeration
- NFS Enumeration
- SMTP Enumeration
System hacking
- Password Cracking
- Password Attacks
- Wire Sniffing
- Password-Cracking Tools
- Vulnerability Exploitation
- Buffer Overflow
- Privilege Escalation
- Privilege Escalation Tools
- Keylogger
- Spyware
Malware threats
- Malware
- Components of Malware
- APT
- Trojan
- Types of Trojans
- Exploit Kits
- Virus
- Virus Lifecycle
- Types of Viruses
- Ransomware
- Computer Worms
Sniffing
- Network Sniffing
- Wiretapping
- MAC Flooding
- DHCP Starvation Attack
- ARP Spoofing Attack
- ARP Poisoning
- ARP Poisoning Tools
Social Engineering
- Social Engineering
- Types of Social Engineering
- Phishing
- Phishing Tools
- Insider Threats/Insider Attacks
- Identity Theft
Denial-of-service
- DoS Attack
- DDoS Attack
- Botnets
- DoS/DDoS Attack Techniques
- DoS/DDoS Attack Tools
- DoS/DDoS Attack Detection Techniques
Session Hijacking
- Session Hijacking
- Types of Session Hijacking
- Spoofing
- Application-Level Session Hijacking
- Man-in-the-Browser Attack
- Client-side Attacks
Evading IDS, Firewalls, and Honeypots
- Intrusion Detection System (IDS)
- Intrusion Prevention System (IPS)
- Firewall
- Types of Firewalls
- Honeypot
- Intrusion Detection Tools
Hacking web services
- Web Server Operations
- Web Server Attacks
- DNS Server Hijacking
- Website Defacement
- Web Cache Poisoning Attack
- Web Server Attack Methodology
Hacking web applications
- Web Application Architecture
- Web Application Threats
- OWASP Top 10 Application Security Risks – 2021
- Web Application Hacking Methodology
SQL injection
- SQL Injection
- Types of SQL injection
- Blind SQL Injection
- SQL Injection Methodology
- SQL Injection Tools
Hacking wireless networks
- Wireless Terminology
- Wireless Networks
- Wireless Encryption
- Wireless Threats
- Wireless Hacking Methodology
- Wi-Fi Encryption Cracking
Hacking mobile platforms
- Mobile Platform Attack Vectors
- OWASP Top 10 Mobile Risks
- App Sandboxing
- SMS Phishing Attack (SMiShing)
- Android Rooting
- Hacking Android Devices
IoT and OT hacking
- IoT Architecture
- IoT Communication Models
- OWASP Top 10 IoT Threats
- IoT Vulnerabilities
- IoT Hacking Methodology
- IoT Hacking Tools
Cloud computing
- Cloud Computing
- Types of Cloud Computing Services
- Cloud Deployment Models
- Fog and Edge Computing
- Cloud Service Providers
- Container
Cryptography
- Cryptography
- Encryption Algorithms
- MD5 and MD6 Hash Calculators
- Cryptography Tools
- Public Key Infrastructure (PKI)
- Email Encryption
- CEH v12 Certification Jobs & Salary -
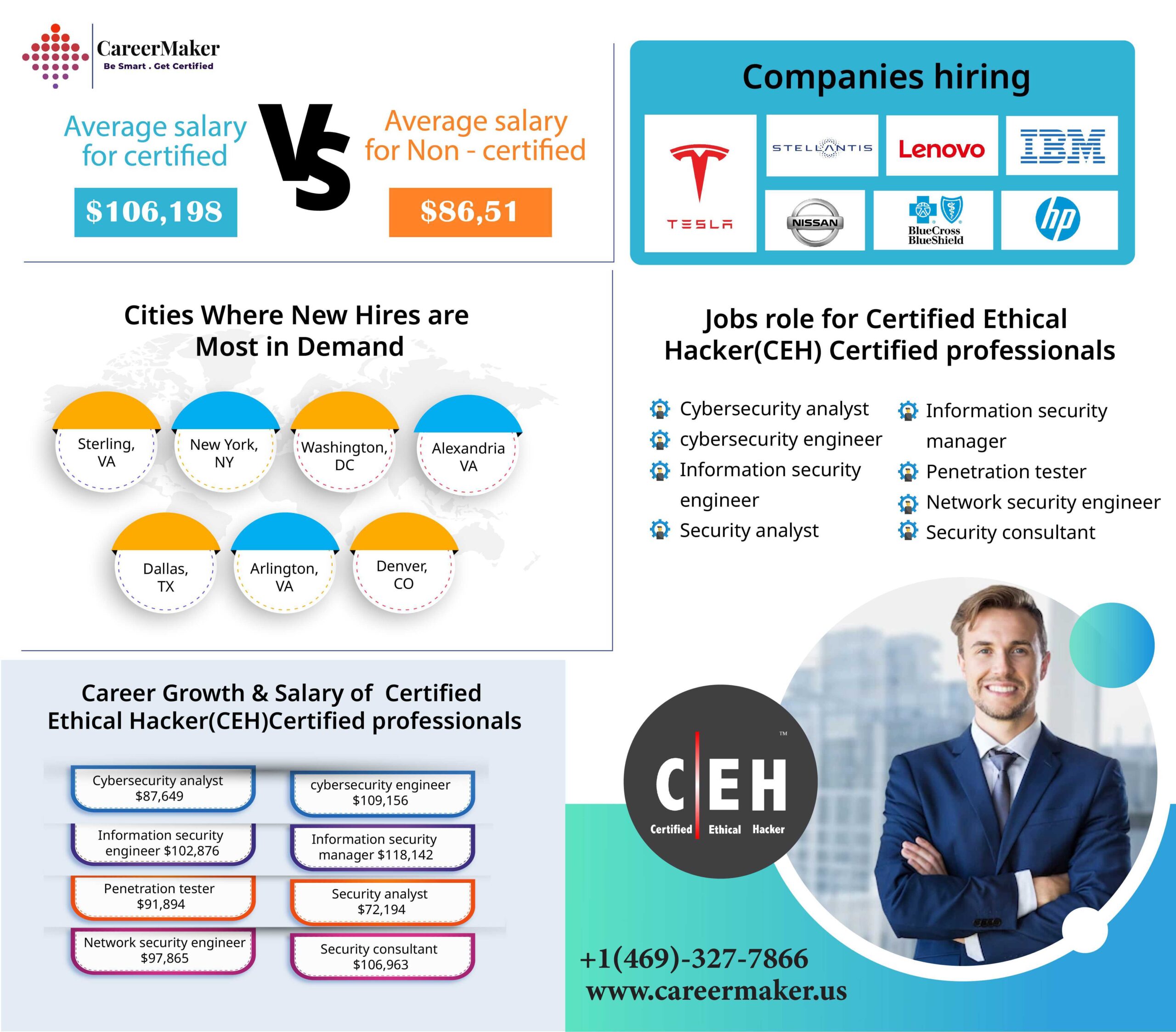
A CEH is a cybersecurity professional who uses ethical hacking techniques to identify vulnerabilities and secure systems, networks, and applications from potential cyber threats.
CEH-certified professionals can hold titles such as Ethical Hacker, Penetration Tester, Security Analyst, Security Consultant, Network Security Engineer, and more.
Yes, CEH-certified professionals often earn competitive salaries due to their specialized skills in identifying and mitigating cyber risks.
- CEH salaries vary based on factors like experience, location, and job role. On average, CEH-certified professionals earn above-average salaries in the cybersecurity field.
Experienced CEH professionals typically command higher salaries, reflecting their expertise in cybersecurity and ethical hacking practices.
Industries such as finance, healthcare, government, and technology value CEH skills and may offer higher salaries to attract top cybersecurity talent.
Yes, the demand for CEH-certified professionals is on the rise as organizations recognize the importance of proactive cybersecurity measures to protect sensitive information.
Absolutely, CEH-certified professionals can advance to roles like Senior Ethical Hacker, Lead Penetration Tester, Security Manager, and Chief Information Security Officer (CISO).
CEH-certified professionals may receive benefits such as bonuses, professional development support, recognition, and opportunities to work on challenging projects.
To maximize earning potential, CEH professionals can specialize in specific cybersecurity domains, gain additional certifications, stay updated with industry trends, and continuously enhance their skills.
- Benefits Of Choosing CareerMaker Solutions ? -
- Our World-Class CERTIFIED INSTRUCTIOR -
- Certification of Course Completion -

- Success Stories -
Become a Certified Ethical Hacker Today -
Don’t miss out on the opportunity to advance your cybersecurity career with our comprehensive certified ethical hacker certification training. Join us today and gain the knowledge and skills needed to excel in the complex world of cybersecurity.
Call Us Today to learn more about our training program, course schedules, and enrollment options. Start your journey towards a successful cybersecurity career today!

- FAQ -
The CEH certification is a globally recognized credential that validates a professional's skills in identifying vulnerabilities and securing systems. It's crucial for ethical hackers who aim to safeguard organizations from cyber threats.
CEH certification opens doors to various cybersecurity roles, such as an ethical hacker, penetration tester, security analyst, and more, due to its validation of expertise in ethical hacking practices.
:CEH-certified individuals can pursue roles like Ethical Hacker, Penetration Tester, Security Consultant, Network Security Engineer, and Security Analyst.
he average salary for CEH-certified professionals varies by location, experience, and industry. On average, it falls within a competitive range in the cybersecurity field.
CEH salaries vary based on factors like experience, location, and job role. On average, CEH-certified professionals earn above-average salaries in the cybersecurity field.
More Experienced CEH professionals typically command higher salaries, reflecting their expertise in cybersecurity and ethical hacking practices.
Industries such as finance, healthcare, government, and technology often value CEH skills and may offer higher salaries to attract top cybersecurity talent.
Yes, the demand for CEH-certified professionals is increasing as organizations prioritize proactive cybersecurity measures to protect sensitive information.
CEH-certified professionals can advance to roles like Senior Ethical Hacker, Lead Penetration Tester, Security Manager, and Chief Information Security Officer (CISO).
Yes, CEH-certified professionals may receive benefits such as bonuses, professional development support, recognition, and opportunities to work on challenging projects.
There are various accredited training programs, online courses, study guides, and practice exams available to assist with CEH exam preparation.
While formal training is recommended, individuals with relevant experience can also choose to study independently using resources like study guides and practice exams.
The CEH exam is multiple-choice and consists of approximately 125 questions that test knowledge and skills related to ethical hacking and cybersecurity.
The CEH exam typically contains around 125 questions and has a duration of 4 hours.
The passing score for the CEH exam varies, but a scaled score of around 70% or higher is generally required to pass.
The CEH exam is primarily multiple-choice and does not include direct practical assessments. However, practical skills are emphasized throughout the certification process.
CEH-certified professionals can engage in continuous learning through industry publications, conferences, webinars, and online courses.
Renewal through continuing education ensures that CEH-certified professionals stay current with industry trends, maintain their expertise, and uphold the value of their certification.
he CEH certification equips professionals with a solid foundation in ethical hacking methodologies, enabling them to identify vulnerabilities, simulate attacks, and secure systems.
Evolving cyber threats, increasing reliance on digital infrastructure, and the need for robust cybersecurity practices are driving the demand for CEH skills.
The CEH curriculum covers a wide range of cybersecurity topics, including emerging threats, ensuring that professionals are well-equipped to address new challenges.
CEH-certified professionals can expect continued growth in demand, expanded leadership roles, and opportunities to contribute to innovative cybersecurity solutions.
CEH-certified professionals can share their knowledge through presentations, blog posts, workshops, and participation in cybersecurity communities, helping advance the field collectively

